Risk Management Enterprise Things To Know Before You Get This
Wiki Article
How Risk Management Enterprise can Save You Time, Stress, and Money.
Table of ContentsRumored Buzz on Risk Management EnterpriseMore About Risk Management EnterpriseThe Ultimate Guide To Risk Management EnterpriseThings about Risk Management EnterpriseFacts About Risk Management Enterprise UncoveredThe smart Trick of Risk Management Enterprise That Nobody is DiscussingRisk Management Enterprise Things To Know Before You Buy
Real-Time Danger Evaluations and Reduction in this software application permit organizations to continually keep an eye on and evaluate dangers as they progress. When risks are identified, the software program facilitates immediate reduction actions.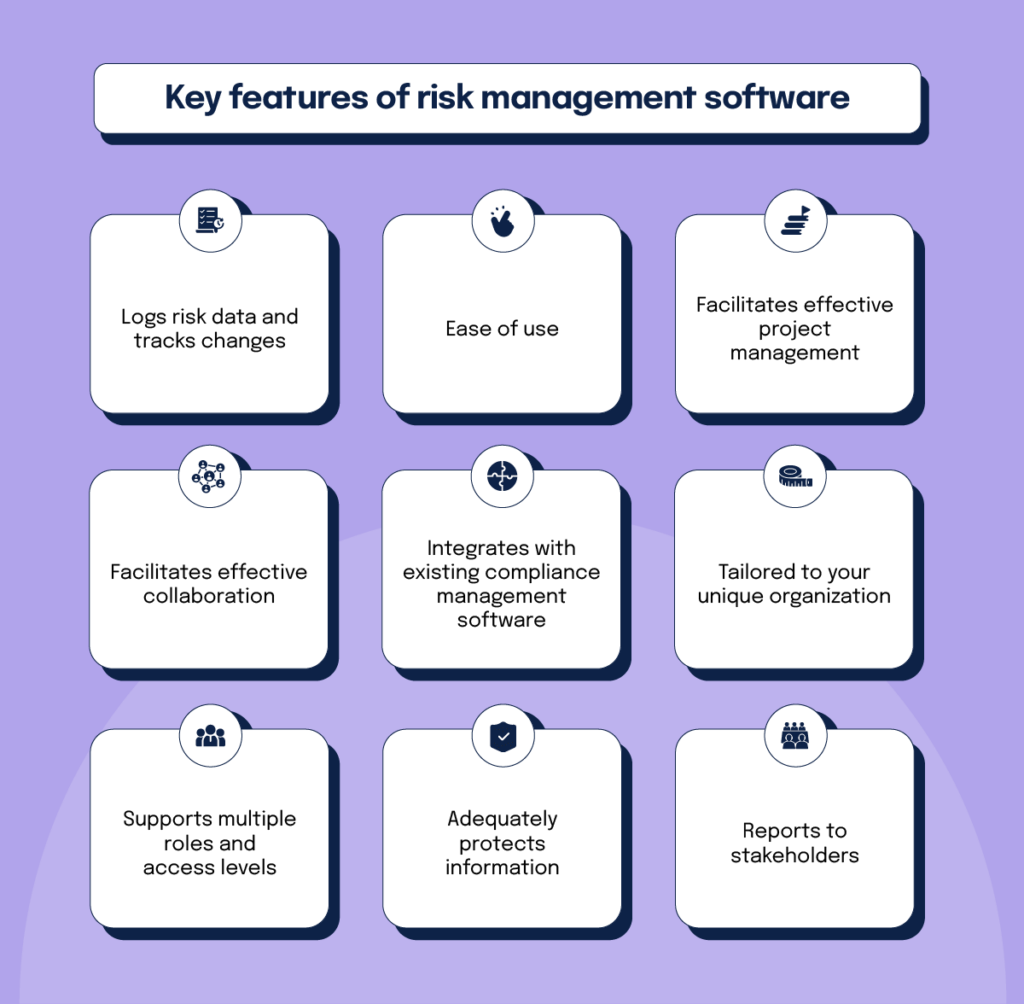
They address the obstacle of continuous danger monitoring by offering devices to monitor dangers constantly. KRIs boost security threat oversight, making certain that prospective risks are identified and taken care of successfully.
Getting The Risk Management Enterprise To Work
IT risk monitoring is a part of venture threat management (ERM), made to bring IT take the chance of in line with an organization's danger hunger. IT run the risk of monitoring (ITRM) incorporates the plans, treatments and innovation essential to decrease dangers and vulnerabilities, while preserving conformity with suitable regulatory needs. On top of that, ITRM looks for to restrict the repercussions of damaging occasions, such as protection violations.While ITRM frameworks supply beneficial assistance, it's easy for IT groups to experience "framework overload." Veronica Rose, ISACA board director and an info systems auditor at Metropol Corp. Ltd., advises using a combination of structures to achieve the most effective outcomes. For example, the ISACA Threat IT framework straightens well with the COBIT 2019 framework, Rose said.
Venture Danger Administration Software Application Advancement: Perks & Characteristics, Price. With technical advancements, risks are constantly on the increase., services browse through a frequently transforming sea of threats.
The Ultimate Guide To Risk Management Enterprise
In this blog, we will certainly dive into the globe of ERM software application, discovering what it is, its advantages, attributes, etc so that you can develop one for your organization. Enterprise Risk Administration (ERM) software program is the application program for preparation, directing, organizing, and regulating business tasks and streamlining danger monitoring processes.With ERM, companies can make insightful decisions to enhance the total resilience of the service. Committed ERM systems are important for companies that frequently deal with vast quantities of delicate info and numerous stakeholders to authorize tactical choices.
: It is demanding for any type of enterprise to undergo an in-depth audit. It can be avoided by using the ERM software program system. This system automates regulation conformity monitoring to keep the company safe and certified. Apart from that, it also logs and classifies all the files in the system making it easier for auditors to assess processes a lot quicker.
8 Easy Facts About Risk Management Enterprise Explained
You can also connect existing software program systems to the ERM by means of APIs or by including data by hand. Businesses can make use of ERM to evaluate risks based upon their possible impact for better danger administration and mitigation.: Including this attribute permits users to obtain real-time alerts on their tools about any type of threat that could take place and its impact.
Instead, the software allows them to set limits for various procedures and send out push alerts in situation of possible threats.: By incorporating data visualization and reporting in the personalized ERM software program, services can get clear understandings concerning risk trends and performance.: It is obligatory for companies to comply with industry compliance and regulative criteria.

These platforms make it possible for companies to carry out best-practice danger monitoring procedures that straighten with sector criteria, offering a powerful, technology-driven technique to recognizing, assessing, and mitigating dangers. This blog checks out the advantages of automated threat administration devices, the areas of threat management they can automate, and the worth they offer an organization.
The Risk Management Enterprise Diaries
Teams can establish kinds with the appropriate areas and easily create various forms for various risk kinds. These danger analysis forms can be distributed for conclusion using automated process that send out alerts to the relevant staff to finish the types online. If types are not finished by the deadline, after that chaser emails are instantly sent by the system.The control monitoring and control testing procedure can additionally be automated. Firms can use computerized operations to send regular control examination notices and team can enter the outcomes using on the internet types. Controls can likewise be checked by the software application by setting guidelines to send informs based upon control information kept in various other systems and spreadsheets that is pulled right into the platform by means of API assimilations.
Risk administration automation software program can additionally sustain with risk reporting for all levels of the venture. Leaders can view reports on danger exposure and control performance via a selection of reporting outcomes including fixed reports, Power BI interactive records, bowtie evaluation, and Monte Carlo simulations. The capability to pull actual time reports at the touch of a switch removes tough data adjustment jobs leaving risk teams with more time to analyze the information and advise the business on the very best strategy.
Organizations operating in affordable, fast-changing markets can not pay for hold-ups or ineffectiveness in attending to possible risks. Typical risk monitoring making use of hands-on spreadsheet-based procedures, while familiar, often lead to fragmented information, time-consuming coverage, and an enhanced likelihood of human mistake.
The Single Strategy To Use For Risk Management Enterprise
This makes certain threat registers are always present and straightened with business purposes. Conformity is another vital vehicle driver for automating threat management. Requirements like ISO 31000, CPS 230 and COSO all offer support around threat monitoring best methods and control structures, and automated threat management tools are structured to straighten with these needs helping companies to fulfill most frequently utilized risk monitoring criteria.Search for risk software program systems with an approvals hierarchy to easily establish operations for threat escalation. This functionality allows you to customize the sight for each and every customer, so they only see the data relevant to them. Make sure the ERM software supplies individual tracking so you can see that entered what information and when.
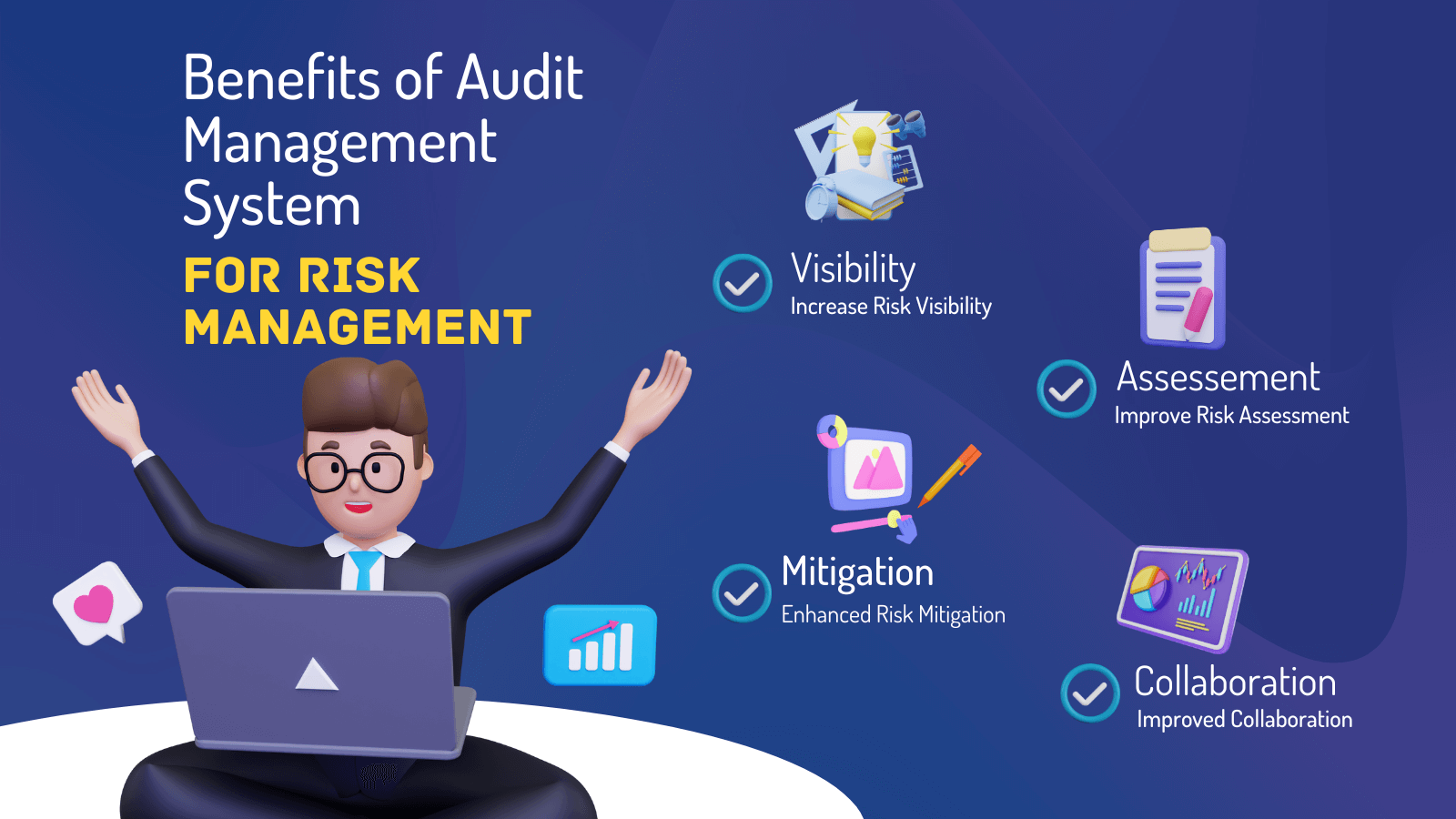
Choose a cloud-based platform to make certain the system gets normal updates from the supplier adding brand-new capability. Choose tools that use task danger management capabilities to handle your projects and portfolios and the connected threats. The advantages of adopting threat administration automation software expand far past performance. Services that integrate these services right into their ERM technique can anticipate a host of concrete and abstract.
Risk Management Enterprise - An Overview
While the situation for automation is engaging, applying a risk administration system is not without its obstacles. For one, information quality is crucial. Automated systems rely upon accurate, up-to-date information to deliver purposeful understandings. To conquer the difficulties of risk management automation, companies have to spend in data cleansing and administration to ensure here a solid foundation for executing an automated platform.Automation in danger administration equips companies to transform their approach to take the chance of and develop a stronger foundation for the future (Risk Management Enterprise). The question is no longer whether to automate threat administration, it's how quickly you can begin. To see the Riskonnect at work,
The solution usually lies in exactly how well risks are expected and handled. Project management software serves as the navigator in the tumultuous waters of task implementation, offering devices that identify and examine dangers and develop methods to alleviate them effectively.
Report this wiki page